Install SSL Certificate on Android, and suddenly, your digital life gains a layer of armor! Imagine a world where your sensitive information, from banking details to personal emails, is shielded from prying eyes. This isn’t a futuristic fantasy; it’s the reality enabled by SSL certificates. We’ll embark on a journey to understand these digital guardians, exploring how they safeguard your data and why they’re essential for anyone navigating the online landscape with an Android device.
From understanding the core principles of SSL/TLS to the practical steps of installation, we’ll traverse the terrain of certificate formats, troubleshoot common hiccups, and uncover the best practices for a secure mobile experience. We’ll delve into the nuances of certificate revocation, the importance of trusted sources, and the art of managing these digital keys with utmost care. Prepare to transform your Android device into a fortress of privacy and security.
Understanding SSL Certificates and Android: Install Ssl Certificate On Android

Hey there, tech enthusiasts! Ever wondered how your Android device keeps your data safe when you’re browsing the web or using apps? Well, a big part of that security comes down to something called SSL certificates. Let’s dive in and unravel this fascinating world, making sure you’re well-equipped to navigate the digital landscape with confidence.
What is an SSL Certificate and Its Function in Securing Data Transmission
An SSL (Secure Sockets Layer) certificate, or its more modern successor, TLS (Transport Layer Security), is essentially a digital passport that verifies a website’s identity. Think of it like a badge of trust that confirms a website is who it claims to be. Its primary function is to encrypt the data transmitted between your Android device and the website’s server.
This encryption scrambles the information, making it unreadable to anyone who might try to intercept it, like a secret code only the intended parties can decipher.Here’s how it works:
- Authentication: The certificate proves the website’s authenticity. When your Android device connects to a website, the server presents its SSL certificate. Your device checks the certificate to ensure it’s valid and issued by a trusted Certificate Authority (CA).
- Encryption: Once the certificate is verified, your device and the server establish a secure, encrypted connection. This means all data exchanged between them, like passwords, credit card details, and personal information, is scrambled, preventing eavesdropping.
- Data Integrity: The certificate ensures that the data hasn’t been tampered with during transmission. If any data is altered, the encryption will fail, alerting the user to a potential security breach.
Consider this:
SSL certificates create a secure tunnel for data, ensuring confidentiality, integrity, and authenticity.
Examples of Scenarios Where SSL Certificates are Crucial for Android Users
SSL certificates are essential for protecting your data in numerous scenarios on your Android device. Here are a few key examples:
- Online Banking: When you access your bank’s website or mobile app, an SSL certificate encrypts your login credentials and financial transactions, protecting your money and personal information from cybercriminals. Imagine the chaos if your banking details were intercepted!
- E-commerce: Shopping online is significantly safer thanks to SSL certificates. They encrypt your credit card information, shipping address, and other sensitive details during the checkout process. Without this protection, your data could be vulnerable to theft, leading to financial loss and identity theft.
- Email Communication: Secure email providers use SSL certificates to encrypt your emails, ensuring that your private messages remain confidential. This prevents unauthorized access to your personal and professional communications.
- Social Media: When you log into social media platforms, SSL certificates protect your username, password, and other personal information from being intercepted. This safeguards your account from being hacked and your data from being misused.
- Web Browsing: Whenever you browse the web, SSL certificates are at work, securing your connection to websites. This ensures that the information you exchange with websites, such as search queries, form submissions, and browsing history, remains private. Look for the “https” in the address bar and the padlock icon to know if a website is using SSL.
Think about the sheer volume of sensitive information we handle on our Android devices daily. Without SSL certificates, all of this data would be exposed to potential threats.
Differences Between SSL, TLS, and Their Relationship to Certificate Security
While the terms SSL and TLS are often used interchangeably, it’s crucial to understand their relationship. SSL is the older protocol, while TLS is its more secure and advanced successor. Both are cryptographic protocols designed to provide secure communication over a network.Here’s a breakdown:
- SSL (Secure Sockets Layer): SSL was the original protocol, developed in the mid-1990s. It was designed to establish a secure connection between a web browser and a web server. However, due to several vulnerabilities and security flaws, SSL is now considered obsolete and is no longer recommended for use.
- TLS (Transport Layer Security): TLS is the successor to SSL. It’s a more secure and robust protocol that addresses the vulnerabilities of SSL. TLS provides stronger encryption algorithms, improved key exchange mechanisms, and better protection against various attacks. TLS is the standard protocol used today for securing online communications.
- Relationship: TLS is essentially an updated and improved version of SSL. Think of it like this: SSL is the older model, and TLS is the newer, more advanced version with better features and security. When you see “SSL” mentioned in modern contexts, it often refers to TLS, as TLS has effectively replaced SSL.
- Certificate Security: Both SSL and TLS rely on digital certificates to verify the identity of websites and encrypt data. The certificates themselves are the same for both protocols. The difference lies in the underlying protocols used to establish and maintain the secure connection. Because TLS is more secure, using a TLS-enabled website provides better protection.
Consider the evolution of technology:
SSL paved the way, but TLS is the current champion in ensuring secure online interactions.
Preparing Your Android Device
Before you dive into installing an SSL certificate on your Android device, it’s essential to get your digital ducks in a row. Think of it like preparing your workspace before starting a complex project – a tidy setup leads to smoother sailing. This section Artikels the essential steps to ready your Android device for the certificate installation process, ensuring a secure and hassle-free experience.
Necessary Steps for Preparation
To ensure a smooth certificate installation, a few preliminary steps are crucial. These steps lay the groundwork for a secure and functional implementation.First, ensure your Android device is updated to the latest available operating system version. Software updates often include critical security patches that address vulnerabilities. You can check for updates in your device’s settings under “System” or “About Phone,” then “Software Update.” The process typically involves downloading and installing the update, followed by a device restart.Next, you need to acquire the SSL certificate in a format compatible with Android, typically a `.crt` or `.pem` file.
This file contains the public key and other vital information about the certificate. You’ll obtain this file from your Certificate Authority (CA) or the source providing the certificate. Ensure you have access to the file on your device, either by downloading it directly or transferring it from another device or computer.Finally, consider the network connection. A stable and reliable internet connection is vital during the installation process.
Ensure your device is connected to a Wi-Fi network or has a strong cellular data signal. This will prevent interruptions during the certificate import and validation steps.
Checking the Current Trust Store
Understanding your device’s existing trust store is crucial before adding a new certificate. This trust store is essentially a collection of pre-installed certificates from trusted Certificate Authorities (CAs). Checking the current state helps avoid conflicts and ensures the new certificate integrates correctly.Accessing the trust store directly on most Android devices is not straightforward. However, you can verify if a specific certificate is already trusted by attempting to access a website that uses that certificate.
If the website loads without any security warnings, the certificate (or the CA that signed it) is likely already trusted. Conversely, if you receive a warning about an untrusted connection, the certificate is not currently recognized.Another method involves using a third-party application designed for managing and inspecting certificates. Several apps available on the Google Play Store allow you to view the contents of the trust store, including the installed certificates and their details.
Use caution when installing such applications and ensure they come from reputable sources.It’s also possible to use command-line tools if your device is rooted or if you have access to the Android Debug Bridge (ADB). ADB allows you to interact with your device from a computer. Using ADB, you can extract the trust store files and examine their contents. However, this method is more technical and requires advanced knowledge.
Settings and Permissions
Before installing a certificate, specific settings and permissions must be in place. These configurations guarantee the certificate is correctly integrated and functions as intended.First, you’ll need to enable the ability to install certificates from external sources. Navigate to your device’s settings, usually under “Security” or “Privacy.” Look for an option related to “Install from storage” or “Install certificates.” You might need to grant the browser or file manager you’ll use to access the certificate file the necessary permissions.
The exact wording and location of these settings may vary slightly depending on your Android version and device manufacturer.Next, consider the network settings. If you plan to use the certificate for a specific Wi-Fi network, you might need to configure the network settings to trust the certificate. Go to the Wi-Fi settings, select the network, and look for options related to “Proxy,” “CA certificate,” or “Security.” Here, you’ll specify the certificate file and configure the necessary settings.Finally, ensure you have the correct permissions for the certificate file itself.
The file should be accessible from your device’s storage. You may need to grant permission to the file manager or browser you’re using to access the file. If you are transferring the certificate from a computer, make sure the file transfer is complete and that the file is not corrupted.
Methods for Installing SSL Certificates
Securing your Android device with an SSL certificate is crucial for protecting your data and ensuring secure communication. Fortunately, Android offers several methods for installing these certificates, each with its own advantages and considerations. Choosing the right method depends on your specific needs and the type of certificate you’re using. Let’s delve into the various ways you can fortify your device’s security.
Installing a Certificate via Device Settings
One of the most straightforward methods for installing an SSL certificate on your Android device is through the device’s settings menu. This approach is generally suitable for installing user certificates, often used for authenticating to internal networks or specific applications.Here’s a step-by-step procedure:
- Obtain the Certificate File: Ensure you have the certificate file in a format supported by Android, typically
.crt,.cer, or.pem. - Transfer the Certificate: Transfer the certificate file to your Android device. You can do this via USB, Bluetooth, email, or a cloud storage service.
- Access Security Settings: Open your device’s Settings app. Navigate to the “Security” or “Security & Location” section. The exact wording may vary depending on your Android version and device manufacturer.
- Find Certificate Settings: Within the Security settings, look for an option related to “Encryption,” “Credentials,” or “Certificates.” Tap on this option.
- Install a Certificate: You should see an option to “Install a certificate” or “Install from storage.” Tap on this option. You may be prompted to enter your device’s PIN, password, or pattern for security.
- Select the Certificate: Browse your device’s storage and select the certificate file you transferred earlier.
- Name the Certificate: You will likely be prompted to give the certificate a name. This helps you identify it later.
- Choose Certificate Usage: Select how the certificate will be used (e.g., for Wi-Fi or VPN).
- Trust the Certificate: Depending on your device, you might be asked to trust the certificate. Make sure you understand the implications before trusting it.
- Verification: Once installed, you can often view the installed certificates in the “Trusted credentials” or “User credentials” section of your security settings.
It is important to understand that the precise steps can vary slightly depending on your Android version and the manufacturer of your device (Samsung, Google Pixel, etc.). However, the general process remains consistent.
Installing a Certificate Using a File Manager
Another method for installing SSL certificates involves using a file manager application on your Android device. This can be a useful alternative, especially if the direct installation method via settings isn’t working as expected or if you prefer a more hands-on approach. This approach is particularly helpful when you need more control over the certificate installation process.Here’s how to do it:
- Get a File Manager: If you don’t already have one, download and install a file manager app from the Google Play Store. Popular choices include Files by Google, Solid Explorer, or ES File Explorer (though be mindful of potential privacy concerns with some third-party apps).
- Obtain the Certificate File: Ensure you have the certificate file (
.crt,.cer, or.pem) on your device. - Locate the Certificate: Use the file manager to navigate to the location where you saved the certificate file.
- Select the Certificate: Tap on the certificate file to select it.
- Choose “Install”: The file manager should offer an “Install” or “Open with” option. Select “Install” (or choose an option that installs certificates).
- Follow the Prompts: The installation process will then guide you through the same steps as the settings method, including providing a name, selecting usage, and confirming trust. You might be redirected to the system settings to complete the process.
- Verification: As with the settings method, you can verify the installation by checking the “Trusted credentials” or “User credentials” section in your device’s security settings.
Using a file manager gives you more control over the file selection process and can sometimes bypass limitations or issues you might encounter with the device settings method.
Comparison of Installation Methods
To summarize the different installation methods and their respective pros and cons, here is a comparative table. This will help you choose the best approach based on your specific needs and situation.
| Method | Pros | Cons |
|---|---|---|
| Device Settings |
|
|
| File Manager |
|
|
Installing Certificates for Specific Apps
Sometimes, you don’t need or want to install a certificate system-wide on your Android device. Perhaps you only need to trust a certificate for a specific app or web browser, like when testing a development environment or accessing a secured internal service. This approach offers more granular control, minimizing the potential security impact of a misconfigured certificate.
Configuring Firefox or Chrome to Trust a Custom SSL Certificate
Web browsers like Firefox and Chrome on Android offer ways to trust custom SSL certificates, allowing secure connections to websites that use self-signed certificates or certificates issued by a private Certificate Authority (CA). The process differs slightly between the two browsers.For Firefox:
- Open Firefox on your Android device.
- Navigate to the website using the custom certificate. Firefox should display a warning indicating an untrusted connection.
- Tap on the lock icon in the address bar.
- Select “View Certificate.”
- Tap on the “Details” tab.
- You’ll see information about the certificate, including the issuer.
- You can’t directly “install” the certificate in Firefox like you can in some desktop versions. Instead, Firefox relies on the Android system’s trusted certificate store, or requires you to add an exception for the specific site. If the CA that signed your certificate is already trusted by Android, Firefox will automatically trust the website. If not, you will see the warning.
You can choose to proceed despite the warning, effectively trusting the certificate for that specific website.
- Be extremely cautious when bypassing security warnings. Ensure you understand the risks associated with trusting a certificate before proceeding. This approach is generally suitable for development and testing environments, but should be carefully considered for production environments.
For Chrome:
- Chrome on Android primarily uses the Android system’s certificate store. If the certificate’s CA is trusted by the Android system, Chrome will automatically trust websites using that certificate.
- If the certificate is not trusted by the Android system, Chrome will display a warning. Unlike Firefox, Chrome doesn’t offer a direct way to bypass this warning or install a certificate specifically for the browser.
- The best approach for Chrome is to ensure the certificate’s CA is trusted at the Android system level.
- To do this, you would need to install the CA certificate as described in the system-wide installation methods.
- Alternatively, if you’re using Chrome for development or testing, consider using a publicly trusted certificate or configuring your development server to use a trusted certificate authority. This avoids the need to install a custom CA certificate on your device.
Configuring a Proxy Server with an SSL Certificate on an Android Device
Setting up a proxy server on your Android device, particularly one that uses SSL encryption, allows you to monitor and filter network traffic. This can be valuable for debugging, security testing, and content filtering. The setup involves configuring the proxy server and configuring your Android device to use the proxy.To configure a proxy server, you generally need the following:
- A proxy server application: Popular choices include tools like Burp Suite, Charles Proxy, or Fiddler. These tools can act as a “man-in-the-middle” (MITM) proxy, allowing you to intercept and inspect HTTPS traffic.
- A certificate for the proxy server: These proxy tools typically generate their own SSL certificates. You’ll need to install the proxy server’s CA certificate on your Android device to trust the proxy’s connections.
- Android device configuration: You need to configure your Android device to use the proxy server. This typically involves entering the proxy server’s IP address and port number in your Wi-Fi network settings.
Here’s a step-by-step guide:
- Install the Proxy Server: Download and install your chosen proxy server application on your computer.
- Generate and Configure the Proxy’s SSL Certificate: The proxy server will generate an SSL certificate. In most cases, you will need to:
- Find the certificate file (usually a .cer or .pem file) generated by the proxy.
- Export the certificate in a format compatible with Android (usually DER or PEM).
- Some proxy tools may automatically generate and install the certificate into the correct keystore on your device, simplifying this step.
- Install the Certificate on Your Android Device: As described in the previous sections, install the proxy server’s CA certificate on your Android device. This makes your device trust the proxy server’s connections.
- Configure Your Android Device to Use the Proxy:
- Go to your Android device’s Wi-Fi settings.
- Find the Wi-Fi network you are connected to and tap on it.
- Look for the “Proxy” settings.
- Select “Manual” or a similar option.
- Enter the proxy server’s IP address and port number. You can usually find this information in the proxy server application’s settings.
- Save the settings.
- Test the Connection: Browse the internet on your Android device. If everything is configured correctly, your traffic will be routed through the proxy server. You should be able to see the requests and responses in the proxy server application.
Remember that using a proxy server, especially one that intercepts encrypted traffic, can have security implications. Only use proxy servers from trusted sources and ensure you understand the risks involved. Also, ensure you are authorized to intercept the traffic.
Troubleshooting Common Issues
Installing SSL certificates on Android, while generally straightforward, can sometimes feel like navigating a maze. Various roadblocks can appear, from cryptic error messages to unexpected app behavior. But fear not! This section will equip you with the knowledge to conquer these challenges, transforming potential headaches into manageable tasks.
Certificate Not Trusted Errors
The dreaded “certificate not trusted” error is a common foe. It typically signals that your Android device doesn’t recognize the certificate authority (CA) that issued the SSL certificate. Think of it as your phone saying, “I don’t know this guy; is he legit?” Several factors can trigger this distrust, and understanding them is the first step toward resolution.When a certificate is untrusted, the Android system prevents secure connections, potentially blocking access to websites or apps that rely on that certificate.
This is a crucial security measure designed to protect user data. However, in certain cases, such as when dealing with self-signed certificates or certificates from less-known CAs, this security feature can become an obstacle.Here’s a breakdown of common causes and solutions:
- The CA is not in the Android’s Trust Store: Android devices come with a pre-installed list of trusted CAs. If the CA that issued your certificate isn’t on this list, your device won’t trust the certificate.
- Solution: Install the CA’s root certificate on your device. This adds the CA to the trust store, allowing your device to recognize and trust certificates issued by that CA. This process usually involves downloading the root certificate (often a .crt or .pem file) and importing it through the device’s settings.
- The Certificate Has Expired: SSL certificates have a defined lifespan. Once the certificate expires, it’s no longer valid, and your device will refuse to trust it.
- Solution: Renew the certificate before it expires and reinstall the updated certificate on your device. Most CAs provide reminders about certificate expiration, making it easier to stay ahead of this issue.
- Incorrect Certificate Chain: An SSL certificate is often part of a chain, including the end-entity certificate (the one for your website or app) and intermediate certificates that link back to a trusted root CA. If the chain is incomplete or improperly configured, the device may not be able to verify the certificate’s authenticity.
- Solution: Ensure that the entire certificate chain is correctly installed on the server where the certificate is being used.
This typically involves including the intermediate certificates along with the end-entity certificate. You can use online tools (like SSL Labs’ SSL Server Test) to check your certificate chain and identify any missing links.
- Solution: Ensure that the entire certificate chain is correctly installed on the server where the certificate is being used.
- Hostname Mismatch: The certificate must be issued for the correct domain or subdomain that you’re trying to access. If the hostname in the certificate doesn’t match the address you’re using, the device will flag it as untrusted.
- Solution: Verify that the certificate is issued for the correct domain or subdomain. If you’re using a wildcard certificate (*.example.com), ensure it covers the specific subdomain you’re accessing.
If not, you’ll need to obtain a certificate specifically for that subdomain.
- Solution: Verify that the certificate is issued for the correct domain or subdomain. If you’re using a wildcard certificate (*.example.com), ensure it covers the specific subdomain you’re accessing.
Incorrect Certificate Formats
Android supports various certificate formats, but using the wrong one can lead to installation failures. The most common formats are PEM (.pem, .crt, .cer) and PKCS#12 (.p12, .pfx). Understanding the differences and how to convert between them is essential.
- PEM Format (.pem, .crt, .cer): This is a text-based format that typically contains the certificate and, sometimes, the private key. It’s the most common format and often used for individual certificates or certificate chains.
- Problem: Attempting to import a PEM-formatted certificate when the system expects a different format.
- Solution: Convert the PEM file to the appropriate format for your device. For instance, if you need a PKCS#12 file, you can use OpenSSL.
OpenSSL pkcs12 -export -in certificate.pem -inkey privatekey.pem -out certificate.p12
- PKCS#12 Format (.p12, .pfx): This is a binary format that can store the certificate, its associated private key, and intermediate certificates, all in a single file. It’s often used for importing certificates and keys into devices or applications.
- Problem: Using the wrong password when importing a PKCS#12 file. PKCS#12 files are usually password-protected for security.
- Solution: Double-check the password you provided when exporting the PKCS#12 file. If you’ve forgotten the password, you may need to regenerate the certificate and private key.
- Unsupported Certificate Type: Android may not support certain certificate types, such as those with unusual key lengths or cryptographic algorithms.
- Problem: The certificate uses a cryptographic algorithm or key length not supported by the Android device.
- Solution: Ensure the certificate uses a supported algorithm and key length. Modern Android versions generally support SHA-256 and higher with key lengths like 2048 bits or greater. You may need to reissue the certificate using a supported configuration.
Certificate Formats and Compatibility

Ah, the wonderful world of digital certificates! Just like choosing the right outfit for a fancy gala, picking the correct certificate format is crucial for your Android device to play nicely with SSL/TLS secured connections. Getting this right is the difference between smooth sailing and a frustrating sea of error messages. Let’s unravel the mystery of certificate formats and how to ensure your Android device speaks the same language as your secure servers.
Supported Certificate Formats
Android, in its infinite wisdom (and with a little help from the standards bodies), supports a few key certificate formats. Understanding these is the first step in your journey to SSL/TLS enlightenment. Here’s a breakdown of the usual suspects:
- .PEM (Privacy Enhanced Mail): This is perhaps the most versatile format. It’s essentially a container that can hold the certificate itself, the private key, or even the entire certificate chain (the certificate, any intermediate certificates, and the root certificate). PEM files are easily identifiable because they start with “—–BEGIN CERTIFICATE—–” and end with “—–END CERTIFICATE—–” (or similar headers/footers for private keys). Think of it as the Swiss Army knife of certificate formats.
- .CRT (Certificate): Often a PEM file, but sometimes just the certificate data itself, encoded in a format like Base64. A .CRT file typically contains the public key and other certificate details. It’s commonly used to store the server’s certificate.
- .CER (Certificate): Similar to .CRT, the .CER extension usually indicates a certificate file, often encoded in DER (Distinguished Encoding Rules) format, which is a binary format. You might find it holding a single certificate or a complete certificate chain.
- .DER (Distinguished Encoding Rules): This is the binary encoding of the certificate. It’s not human-readable like PEM. While not directly installed, Android can understand certificates in this format, especially when they are part of a PKCS#12 file.
- .PKCS#12 (.PFX or .P12): This format is a container for the certificate and the private key, often password-protected. It’s useful when you need to import both the certificate and the private key into your Android device (e.g., for client authentication). This is like a secure package, safeguarding both the public and private components.
Converting Between Certificate Formats
Sometimes, you’ll find yourself with a certificate in one format and your Android device craving another. Fear not! Conversion tools are readily available. These tools are your trusty sidekicks in the battle against format incompatibility.
Here’s how you can typically convert between formats using OpenSSL, a powerful command-line tool (often available on Linux, macOS, and Windows via tools like Cygwin or WSL):
- Converting .PEM to .DER:
- Converting .DER to .PEM:
- Converting .PFX/.P12 to .PEM:
- Converting .PEM to .PFX/.P12:
openssl x509 -in certificate.pem -out certificate.der -outform DER
This command takes a .PEM file as input and outputs a .DER file.
openssl x509 -in certificate.der -inform DER -out certificate.pem -outform PEM
This converts a .DER file to .PEM.
openssl pkcs12 -in certificate.p12 -out certificate.pem -nodes
You’ll likely be prompted for the password of the .p12 file. The -nodes option prevents the private key from being encrypted in the output .PEM file (use this carefully; encrypt the key if security is paramount).
openssl pkcs12 -export -in certificate.pem -inkey private.key -out certificate.p12
This assumes you have both the certificate (certificate.pem) and the private key (private.key). You will be prompted to set a password for the .p12 file.
Note: These commands assume you have OpenSSL installed and configured on your system. Also, always handle private keys with extreme care. Keep them secure, and never share them publicly.
Verifying Certificate Format and Compatibility
Before you go ahead and install a certificate, it’s wise to double-check its format and make sure your Android device will accept it. Think of it as a quality control check before the big day. There are a few ways to accomplish this.
- Checking the File Extension: This is the simplest check. If the file ends in .PEM, .CRT, or .CER, you’re likely dealing with a certificate file. .PFX or .P12 suggests a PKCS#12 file containing both the certificate and private key.
- Using a Text Editor: Open the certificate file in a text editor. If you see “—–BEGIN CERTIFICATE—–” and “—–END CERTIFICATE—–”, it’s a PEM file. This quick inspection can save you a lot of headaches.
- Using OpenSSL (Again!): OpenSSL can also help you inspect the certificate’s contents and format.
- Android Device Compatibility Testing: The ultimate test is, of course, to try installing the certificate on your Android device. If it installs without errors, you’re golden! If not, you might need to convert the format.
openssl x509 -in certificate.pem -text -noout
This command displays the certificate details in a human-readable format, including the issuer, subject, validity period, and public key. It works with PEM, CRT, and CER files.
Example: Let’s say you’re trying to install a certificate for a website. You download a file called “website.crt”. You open it in a text editor and see the “BEGIN CERTIFICATE” and “END CERTIFICATE” markers. This suggests it’s a PEM-formatted certificate, which is highly compatible with Android. You then try to install it on your Android device, and it works perfectly.
Success!
Security Considerations and Best Practices
Navigating the digital landscape on your Android device demands a keen understanding of security protocols, especially when dealing with SSL certificates. These certificates are the digital keys that unlock secure communication channels, but they can also be a point of vulnerability if handled carelessly. This section delves into the critical aspects of secure certificate management, ensuring your data remains protected from prying eyes.
Importance of Trustworthy Certificate Sources
The bedrock of secure SSL certificate installation lies in the trustworthiness of the source. Think of it like this: You wouldn’t accept a key to your house from a stranger, would you? Similarly, you should only install certificates from entities you genuinely trust. Certificates from untrusted sources pose significant risks, potentially allowing malicious actors to intercept your data, impersonate legitimate websites, or launch sophisticated attacks.
Secure Storage and Management of SSL Certificates
Protecting your SSL certificates is akin to safeguarding your digital identity. Implementing robust storage and management practices is crucial to mitigate potential threats. This involves a multi-layered approach, encompassing secure storage, regular backups, and controlled access. Consider the following:
- Password Protection: Always password-protect your certificate files. A strong, unique password is the first line of defense. Think of it as the lock on your digital vault.
- Secure Storage Location: Store certificates in a secure location on your device. This might involve using a dedicated certificate store or a password-protected file manager. Avoid storing them in easily accessible folders.
- Regular Backups: Create regular backups of your certificates. In the event of data loss or device failure, you can restore your certificates and maintain secure connections.
- Access Control: Limit access to your certificates. Only authorized personnel should be able to view, modify, or delete them. This minimizes the risk of unauthorized access and potential misuse.
- Device Encryption: Enable device encryption. This encrypts all data on your device, including certificates, protecting them even if your device is lost or stolen.
Potential Risks of Installing Untrusted Certificates
Installing certificates from unknown or untrusted sources opens the door to a host of security vulnerabilities. It’s like inviting a wolf in sheep’s clothing into your digital ecosystem. These risks can have severe consequences, ranging from data breaches to identity theft. Some of the primary dangers include:
- Man-in-the-Middle Attacks (MitM): Untrusted certificates can be used to perform MitM attacks. This allows attackers to intercept and decrypt your communications, stealing sensitive information such as usernames, passwords, and financial data. Imagine someone eavesdropping on your conversations and stealing your secrets.
- Phishing Attacks: Malicious actors can use untrusted certificates to create fake websites that appear legitimate. They can then trick you into entering your credentials, leading to phishing attacks. This is like receiving a fake email from your bank, designed to steal your account details.
- Malware Distribution: Untrusted certificates can be used to sign malicious software, making it appear trustworthy. When you install this software, it can compromise your device and steal your data. This is akin to accepting a gift from a stranger that contains a hidden, dangerous surprise.
- Data Breaches: Compromised certificates can lead to data breaches. Attackers can exploit vulnerabilities to gain access to your data, leading to the exposure of sensitive information.
Best Practices for Secure Certificate Management
Implementing these best practices will help you to create a robust security posture and protect your data. This table encapsulates key strategies for secure certificate management:
| Type of Best Practice | Description | Benefits |
|---|---|---|
| Verify Certificate Authority (CA) | Always verify the Certificate Authority (CA) that issued the certificate. Ensure the CA is a trusted and reputable entity. Check the certificate details for the issuer’s name and verify it against a list of known, trusted CAs. | Reduces the risk of using certificates from fraudulent or compromised CAs, ensuring that the certificate originates from a legitimate source. |
| Use Strong Passwords | Protect certificate files with strong, unique passwords. Avoid using easily guessable passwords, such as personal information or common phrases. Consider using a password manager to generate and store strong passwords. | Prevents unauthorized access to certificate files, even if the device or storage location is compromised. Strong passwords are the first line of defense against brute-force attacks. |
| Regularly Update Certificates | Ensure certificates are regularly updated. Certificates have an expiration date. When a certificate expires, secure connections will be interrupted. Set reminders to renew certificates before they expire. | Maintains the security of your connections. Expired certificates can disrupt services and expose your data to risks. Regular updates also include the latest security enhancements. |
| Monitor Certificate Usage | Regularly monitor certificate usage. Review logs to identify any unauthorized access or unusual activity. Set up alerts to notify you of any suspicious behavior, such as attempts to access certificate files. | Helps detect and respond to potential security breaches. Early detection allows you to take immediate action, minimizing the impact of any security incidents. |
Certificate Revocation and Renewal
Certificates are like digital passports, vouching for the identity of websites and ensuring secure connections. But sometimes, these digital passports get lost, stolen, or simply expire. This is where certificate revocation and renewal come into play, crucial aspects of maintaining a secure browsing experience on your Android device.
Certificate Revocation: Understanding the Risks
Certificate revocation is the process of invalidating a previously issued SSL certificate before its expiration date. This happens when a certificate is compromised, the private key is leaked, or the certificate authority (CA) that issued the certificate deems it untrustworthy. Revocation prevents malicious actors from using the compromised certificate to impersonate legitimate websites and intercept your data. The impact on Android devices can be significant, potentially blocking access to websites or apps that rely on the revoked certificate.
If a certificate is revoked, your device will display an error message, warning you about the potential security risk.To understand the implications, imagine you’re trying to visit your bank’s website. If the bank’s certificate is revoked, your Android device will refuse to connect, displaying an error. This is because your device trusts the CA that issued the certificate, but that CA has now declared the certificate invalid.
Checking Certificate Revocation Status
It’s vital to verify if a certificate has been revoked. While Android handles revocation checks automatically in many cases, manually verifying can provide an extra layer of security.
- Using the Browser: Most Android browsers, like Chrome and Firefox, perform revocation checks automatically. When you visit a website, the browser checks the certificate’s status. If the certificate is revoked, the browser will display a warning and prevent you from accessing the site.
- Certificate Transparency Logs: Certificate Transparency (CT) logs are public, append-only logs of issued SSL/TLS certificates. You can use online tools or browser extensions to check if a certificate is present in CT logs and whether it has been revoked. This method offers a more detailed view of the certificate’s status.
- Certificate Authority’s CRL/OCSP: Certificate Authorities (CAs) maintain Certificate Revocation Lists (CRLs) or use Online Certificate Status Protocol (OCSP) to provide real-time revocation information. You can use online tools or consult the CA’s documentation to check a certificate’s revocation status.
Checking for revocation is like double-checking your lock before you leave the house; it’s an extra step to ensure your security.
Renewing SSL Certificates on Android
Renewing an SSL certificate is essential to maintaining secure connections, especially when the certificate nears its expiration date. While Android users typically don’t directly renew certificates for websites (that’s the website owner’s responsibility), they need to be aware of the process and how it affects their browsing experience. The process involves generating a new certificate and installing it on the web server.
When the certificate is renewed, the website owner installs the new certificate on the server, and the Android device will automatically trust it, assuming the new certificate is issued by a trusted CA.The process typically unfolds as follows:
- Website Owner’s Action: The website owner generates a new certificate signing request (CSR) and submits it to a Certificate Authority (CA).
- Certificate Issuance: The CA verifies the website owner’s identity and issues a new SSL certificate.
- Certificate Installation: The website owner installs the new certificate on the web server.
- Android Device’s Role: When an Android device connects to the website after the certificate renewal, the device verifies the new certificate’s validity, including its expiration date, and trusts the connection if the certificate is issued by a trusted CA.
Imagine your favorite online store renewing its security certificate. When you next visit, your Android device automatically verifies the new certificate, ensuring a continued secure shopping experience. The process is seamless, as long as the website owner renews the certificate and installs it correctly.
Visual Guides and Illustrations
Let’s face it: sometimes, words just aren’t enough. When dealing with technical processes, a picture truly is worth a thousand keystrokes. This section dives into the visual aids that make understanding SSL certificate installation on Android a breeze, ensuring you can confidently navigate the process. These illustrations are designed to be clear, concise, and easy to follow, transforming complex steps into a straightforward visual journey.
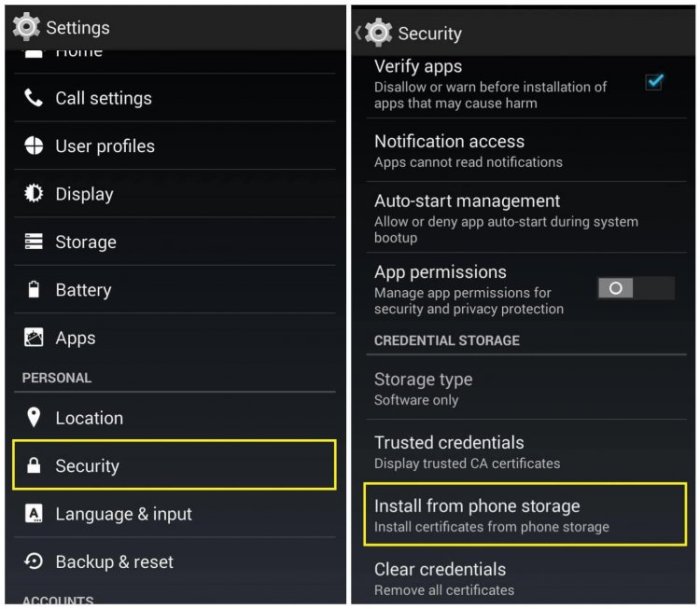
Importing an SSL Certificate into Android Settings
The Android settings menu can sometimes feel like a labyrinth. That’s why a clear visual guide is essential.Imagine an illustration depicting the process of importing an SSL certificate within the Android settings menu. The illustration should consist of a series of sequential panels, each representing a step in the process.* Panel 1: The Android Settings Icon. This panel shows the iconic Android settings gear icon, prominently displayed on a typical Android home screen.
A small arrow points from the home screen to the settings icon, emphasizing where to begin.* Panel 2: Navigating to Security Settings. This panel zooms in on the settings menu. A visual representation of the menu, with a list of options, is shown. A highlighted rectangle encompasses the “Security” or “Security & Location” option (the specific wording may vary slightly depending on the Android version).
An arrow points from the settings menu to this option.* Panel 3: Accessing Certificate Settings. This panel shows the “Security” menu. Inside this menu, a section labeled “Encryption” or “Credentials” (again, the specific name can vary) is displayed. Within this section, the “Certificate management” or “Trusted credentials” option is highlighted with an arrow pointing to it.* Panel 4: Importing the Certificate. This panel zooms into the certificate management settings.
Here, a button labeled “Install a certificate” or a similar phrase, perhaps represented by a plus sign icon or an “Import” button, is prominently displayed. An arrow indicates the user’s action to tap or click this button.* Panel 5: File Selection. This panel shows a file selection dialog, typical of Android. It displays a list of file managers or storage locations (internal storage, SD card, etc.).
The illustration should show a user selecting a specific file manager (e.g., “Files by Google”) and navigating to the location where the certificate file (e.g., a `.crt` or `.pem` file) is stored. A small arrow indicates the selection and file navigation.* Panel 6: Certificate Details and Confirmation. This panel shows the certificate details. This includes the certificate’s name, the issuing authority, and validity dates.
It should also include a button labeled “OK” or “Install” to confirm the installation. A checkmark icon might appear next to the certificate name after installation.This entire illustration uses clear icons, bold text labels, and directional arrows to guide the user through each step, ensuring a user-friendly and easily understandable visual representation of the certificate import process.
Installing a Certificate via File Manager, Install ssl certificate on android
Installing a certificate through a file manager offers another convenient method, especially for users who prefer a more hands-on approach.An illustration can show the steps for installing a certificate via a file manager, including icons and UI elements.* Panel 1: The File Manager Icon. The illustration starts with a depiction of a typical Android home screen, showing a file manager app icon (e.g., “Files,” “My Files,” or similar).
An arrow points from the home screen to the file manager icon.* Panel 2: Locating the Certificate File. The illustration zooms into the file manager interface. The user is shown navigating the file system, selecting the location where the certificate file (e.g., `.crt`, `.pem`, or `.der`) is stored. A visual representation of a file folder structure, with clearly labeled folders and file names, is included.* Panel 3: Selecting the Certificate File. The illustration highlights the certificate file within the file manager.
The file name is shown with a clear visual cue, such as a different color background or a checkmark icon, to indicate selection. An arrow points from the file to the next step.* Panel 4: The “Open With” Menu. When the certificate file is selected, the illustration shows the “Open with” or “How do you want to open this?” prompt that typically appears in Android.
Options such as “Certificate installer,” “Install certificate,” or similar are displayed.* Panel 5: Certificate Installation Prompt. The illustration depicts the Android system’s certificate installation prompt. This might include the certificate’s name, issuing authority, and a prompt to name the certificate and choose the certificate’s purpose (e.g., “VPN and apps” or “Wi-Fi”). Fields for entering the certificate name and selecting the usage are clearly shown.* Panel 6: Confirmation and Success. The final panel shows the certificate successfully installed, often represented by a notification or a change in the user interface, such as the certificate now appearing in the “Trusted credentials” section of the Android settings.
A checkmark next to the certificate indicates the successful installation.This illustration utilizes recognizable UI elements, such as file icons, file manager navigation, and system prompts, to provide a clear and intuitive guide to installing a certificate via a file manager.
Trusted vs. Untrusted Certificates in a Web Browser
Understanding the visual cues that distinguish a trusted from an untrusted certificate is crucial for maintaining online security.An illustration demonstrates the difference between a trusted and an untrusted certificate in an Android web browser, with clear visual cues.* Panel 1: The Secure Connection Icon (Trusted). The first panel shows a web browser’s address bar with a website address. A padlock icon (🔒) is prominently displayed to the left of the website address (e.g., `https://example.com`).
The padlock is colored green and is closed. This indicates a secure connection with a trusted certificate. A small label near the padlock says, “Connection is secure.”* Panel 2: The Secure Connection Details (Trusted). The illustration shows what happens when a user taps the padlock icon. A pop-up or a small informational panel appears, indicating the connection is secure. It includes information such as the website’s identity (the domain name), the certificate issuer (e.g., “Let’s Encrypt”), and the validity period.* Panel 3: The Warning Icon (Untrusted). The next panel shows the same web browser address bar, but now, instead of a green padlock, a warning icon is displayed.
This icon could be an open padlock (🔓), a red padlock (🔒), or a triangle with an exclamation point (⚠). The address bar might also display a message such as “Not secure” or “Your connection is not private.”* Panel 4: The Warning Details (Untrusted). The illustration shows what happens when the user taps the warning icon. A pop-up or informational panel appears, explaining that the connection is not private.
It states the reason for the untrusted certificate, such as “This website’s security certificate is not trusted,” “The certificate is expired,” or “The certificate is not valid for this site.” The panel might offer options to view the certificate details (for advanced users) or to proceed to the website (with a warning that the connection is not secure).* Panel 5: Additional Warning Detail (Untrusted). This panel further shows the details about the certificate problem.
It may indicate the certificate issuer is unknown or that the certificate has been revoked. A prominent warning message is included to alert the user of potential risks.This illustration uses clear and universally understood icons, color coding (green for trusted, red/yellow for untrusted), and concise text labels to clearly demonstrate the visual differences between a trusted and an untrusted certificate, empowering users to make informed decisions about their online security.
