Easy methods to unlock my android telephone with out pin – Embark on a journey into the digital labyrinth, the place forgotten PINs and locked screens can really feel like an insurmountable problem. Concern not, for we’re about to unveil the secrets and techniques to unlocking your Android telephone with out that pesky PIN standing in your means. We’ll delve into the widespread situations that result in this predicament – perhaps you have had a reminiscence lapse, or maybe a mischievous buddy has set a lock you may’t recall.
We’ll additionally gently contact upon the potential pitfalls of unauthorized entry, guaranteeing you are well-equipped to navigate this example responsibly. Contemplate this your digital rescue guide, a pleasant companion guiding you thru the maze.
This is not only a technical walkthrough; it is a story of problem-solving, resilience, and reclaiming entry to your valuable digital life. We’ll discover varied strategies, from the acquainted consolation of your Google Account to the extra adventurous path of Android Debug Bridge (ADB). You may uncover the facility of ‘Discover My System,’ be taught the intricacies of manufacturing unit resets, and even take into account the potential of biometric authentication.
Alongside the way in which, we’ll equip you with the data to troubleshoot widespread points and, most significantly, present preventative measures to make sure you’re by no means locked out once more. Let’s get began!
Introduction: Understanding the Drawback
Let’s face it, we have all been there. That sinking feeling whenever you stare at your Android telephone, the PIN staring again at you, and your thoughts drawing a whole clean. It is a irritating scenario, however a typical one. Forgetting your PIN can vary from a minor inconvenience to a significant headache, relying on the circumstances. Understanding why this occurs and what’s at stake is step one towards discovering an answer.
Frequent Causes of PIN Amnesia
The human mind is a humorous factor. It prioritizes info primarily based on frequency and significance. PINs, sadly, typically fall into the “sometimes used” class, particularly you probably have a telephone with biometric safety. Couple that with a busy schedule, a distracted second, or just a reminiscence lapse, and
poof* – the PIN vanishes into the digital ether.
Listed below are some typical culprits:
- Rare Use: When you primarily use fingerprint or facial recognition, you may solely enter your PIN sporadically, making it tougher to recollect.
- Cognitive Overload: A traumatic day, multitasking, or just having an excessive amount of in your thoughts can cloud your reminiscence.
- Password Fatigue: We juggle numerous passwords and PINs each day. The mind can generally jumble them up.
- Modifications in Routine: Altering your telephone utilization patterns, like touring or utilizing a brand new app, can set off a reminiscence lapse.
- Easy Forgetfulness: Let’s be trustworthy, generally we simply overlook!
Situations Requiring PIN Bypass
There are many real-world situations the place unlocking your telephone with out the PIN turns into essential. Think about these conditions:
- Misplaced or Stolen Telephone: It’s essential to entry your telephone remotely to trace it, erase knowledge, or contact the authorities. Time is of the essence!
- Forgotten PIN After a Lengthy Break: Maybe you have been utilizing a unique gadget for some time, and your PIN has slipped your thoughts.
- System Harm: A cracked display or a malfunctioning touchscreen makes PIN entry unimaginable, however you must retrieve necessary info.
- Medical Emergency: First responders may want entry to your telephone for emergency contacts or medical info.
- Deceased Relative’s Telephone: Accessing a liked one’s telephone to retrieve reminiscences, pictures, or necessary knowledge after their passing could be a delicate and mandatory process.
Potential Dangers of Unauthorized Entry
Whereas the necessity to bypass a PIN might be legit, it is essential to acknowledge the dangers concerned. Accessing a locked telephone with out authorization opens the door to a number of potential issues.
- Information Breach: Private info, together with contacts, pictures, emails, and monetary particulars, might be compromised.
- Id Theft: Hackers might use your knowledge to impersonate you, open fraudulent accounts, or commit different types of id theft.
- Privateness Violations: Your personal communications, searching historical past, and site knowledge might be uncovered.
- Authorized Penalties: Unauthorized entry to another person’s telephone might end in authorized motion, relying on the circumstances and native legal guidelines.
- Malware An infection: If the telephone’s safety is compromised, it might turn out to be susceptible to malware, resulting in additional knowledge loss or system injury.
Due to this fact, it is essential to method any try and unlock a telephone with out a PIN with warning and solely when you’ve gotten a legit and moral motive to take action.
Strategies Utilizing Google Account
Alright, let’s dive into how your Google account might be your digital knight in shining armor whenever you’re locked out of your Android telephone. It is a lifesaver, actually, and figuring out this could prevent from a significant headache. The Google Account technique leverages the facility of the cloud and your telephone’s connection to it.
Discover My System Characteristic and Its Function
Discover My System is Google’s built-in software, basically your telephone’s private detective. It is designed that will help you find, safe, and even wipe your Android gadget if it is misplaced or stolen. The function depends on a number of key parts to perform. Firstly, your telephone must be powered on and related to the web, both by way of Wi-Fi or cellular knowledge. Secondly, your Google account have to be signed in on the gadget.
Thirdly, the Discover My System function have to be enabled in your telephone’s settings. Consider it as a digital security web, consistently pinging your telephone’s location and able to spring into motion when wanted.
Steps to Use Discover My System to Remotely Unlock a Telephone
The method of utilizing Discover My System to unlock your telephone is pretty simple, however it requires some preliminary setup. It is like having a key, however you must be sure to have it, and the door is unlocked to make use of it.
Here is a breakdown:
First, you will want one other gadget, like a pc, pill, or one other telephone. On this gadget, open an online browser and go to the Discover My System web site.
You may have to log in to the Google account related along with your locked telephone. As soon as logged in, you need to see a map displaying the approximate location of your telephone.
Subsequent, choose your locked gadget from the record of gadgets related along with your Google account. You may then be introduced with a number of choices: play sound, safe gadget, and erase gadget.
To unlock your telephone, choose “Safe gadget.” This feature lets you set a brand new lock display password.
You may be prompted to enter a brand new password and make sure it. You can even embody a restoration message and telephone quantity, which might be useful if somebody finds your telephone.
After you have set the brand new password, your telephone ought to replace and you’ll use the brand new password to unlock your telephone. It’d take a couple of minutes for the adjustments to sync.
Keep in mind the conditions:
- Your telephone have to be powered on.
- Your telephone have to be related to the web (Wi-Fi or cellular knowledge).
- Your Google account have to be signed in in your telephone.
- The Discover My System function have to be enabled in your telephone. That is often enabled by default, however it’s value double-checking in your telephone’s settings beneath “Safety” or “Google”.
It is necessary to do not forget that this technique works by overriding your present lock display. This implies for those who had a sample, PIN, or password set earlier than, will probably be changed by the brand new one you set utilizing Discover My System.
Potential Limitations of the Google Account Technique
Whereas the Google Account technique is a robust software, it does have its limitations. It isn’t a magic wand, sadly.
One of many greatest constraints is that your telephone must be related to the web. In case your telephone is offline, Discover My System will not have the ability to talk with it, and you will not have the ability to remotely unlock it.
This could be a main hurdle in case your telephone is in an space with no Wi-Fi or mobile service.
One other potential limitation is that the telephone have to be powered on. If the battery is lifeless, or if somebody has turned off the gadget, Discover My System will not have the ability to find it or unlock it. Because of this it is essential to behave quick for those who understand your telephone is locked and you may’t bear in mind the PIN or password.
Moreover, if somebody has already manufacturing unit reset your telephone, all the info might be worn out, and the Discover My System technique will not have the ability to unlock it.
Additionally, take into account that the Discover My System function may not at all times be 100% correct in pinpointing your telephone’s location. The accuracy will depend on elements similar to GPS sign energy and the provision of Wi-Fi networks.
Lastly, this technique is barely relevant you probably have a Google account related along with your gadget and have enabled Discover My System beforehand. With out these, you’re out of luck utilizing this particular technique.
Utilizing Android Debug Bridge (ADB)
Superior Technique
Superior Technique
Generally, you end up locked out, and the same old tips simply will not reduce it. That is the place the Android Debug Bridge (ADB) comes into play. It is a highly effective software, a digital Swiss Military knife, for interacting along with your Android gadget. It isn’t for the faint of coronary heart, however with the precise steps, it may be a lifesaver.
ADB is a command-line utility that allows you to talk along with your Android gadget out of your pc. Consider it as a direct line of communication, bypassing the same old consumer interface. This may be extremely helpful whenever you’re locked out of your telephone and have to entry its inside programs. It provides a degree of management that goes far past the usual choices out there in your gadget’s display.
Android Debug Bridge (ADB) Perform and Necessities
ADB acts as a bridge, enabling communication between your pc and your Android gadget. It is a part of the Android SDK (Software program Growth Package) and is often utilized by builders for debugging and testing purposes. Nevertheless, its capabilities lengthen to unlocking your gadget in particular situations. To make use of ADB successfully, a number of necessities have to be met. Firstly, you will want a pc with ADB put in.
This often entails downloading the Android SDK Platform-Instruments package deal from the official Android Builders web site and organising the required atmosphere variables. Secondly, you want the proper USB drivers in your Android gadget put in in your pc. These drivers permit your pc to acknowledge and talk along with your telephone. Lastly, and crucially, USB debugging have to be enabled in your gadget earlier than you get locked out.
If you have not enabled it beforehand, this technique will not work. Consider it as needing a key to unlock the door; with out the important thing (USB debugging), you are out of luck.
Step-by-Step Process to Unlock a Telephone Utilizing ADB, Easy methods to unlock my android telephone with out pin
When you’ve got enabled USB debugging earlier than being locked out, ADB could be a viable resolution. Right here’s how one can try and unlock your telephone utilizing ADB. Please do not forget that this technique may not work on all gadgets, and its success will depend on your gadget’s configuration and whether or not you have beforehand enabled USB debugging. First, join your Android gadget to your pc utilizing a USB cable.
Then, open a command immediate or terminal window in your pc and navigate to the listing the place you’ve gotten put in ADB (often the platform-tools folder). The following step is to test in case your gadget is acknowledged by ADB. Kind the command:
adb gadgets
This command will record all related Android gadgets. In case your gadget is listed, you may proceed. If not, double-check your USB connection, gadget drivers, and guarantee USB debugging is enabled (for those who had the foresight to take action). Now, you will attempt to take away the sample lock or password. Use one of many following instructions, relying in your gadget’s lock sort.
Attempt these instructions in sequence, as one may work the place one other would not:
To take away the sample lock
adb shell rm /knowledge/system/gesture.key
To take away the password or PIN
adb shell rm /knowledge/system/password.key
After executing the command, reboot your telephone. You are able to do this by typing:
adb reboot
When your telephone restarts, the lock display needs to be gone, or not less than you need to have the ability to bypass it. You may have to arrange a brand new lock display sample or password afterward. If these instructions fail, it is attainable that your gadget has a unique safety implementation, or that USB debugging was not enabled. For instance, think about you’re utilizing a Samsung Galaxy S23.
You’ve gotten ADB put in in your Home windows pc, and you’ve got related your telephone by way of USB. You enter the command “adb gadgets” within the command immediate, and your gadget is listed. You then run the “adb shell rm /knowledge/system/gesture.key” command, adopted by “adb reboot.” After the reboot, the sample lock is gone. You may then arrange a brand new lock sample.
The Want for Enabling USB Debugging Beforehand
Enabling USB debugging is the one most necessary prerequisite for utilizing ADB to unlock your telephone. With out it, ADB merely can not talk along with your gadget at a low sufficient degree to take away the lock display. It is like attempting to begin a automotive with out the important thing. USB debugging permits your pc to entry the gadget’s inside capabilities, which is important for executing the ADB instructions.
If USB debugging wasn’t enabled earlier than you bought locked out, ADB will not have the ability to bypass the safety measures. It is a essential safety function designed to guard your gadget from unauthorized entry. The choice is often discovered throughout the Developer choices in your telephone’s settings. To allow it, you sometimes have to go to “Settings” -> “About telephone” and faucet on the “Construct quantity” a number of instances till developer choices are unlocked.
Then, throughout the Developer choices, you may allow USB debugging.
Frequent ADB Instructions and Their Features for Telephone Unlocking
ADB gives a spread of instructions that can be utilized to work together along with your Android gadget. Whereas many are designed for builders, a number of might be significantly useful in unlocking a locked telephone, if USB debugging was enabled beforehand. The desk under Artikels some widespread ADB instructions and their particular capabilities on this context. Keep in mind, the success of those instructions will depend on your gadget and its safety configuration.
| Command | Perform | Vital Concerns | Instance |
|---|---|---|---|
| adb gadgets | Lists all related Android gadgets. | Ensures your gadget is acknowledged by ADB. | Open command immediate, sort “adb gadgets”, press Enter. |
| adb shell rm /knowledge/system/gesture.key | Makes an attempt to take away the sample lock. | Could not work on all gadgets; requires USB debugging. | adb shell rm /knowledge/system/gesture.key |
| adb shell rm /knowledge/system/password.key | Makes an attempt to take away the password or PIN lock. | Related limitations because the gesture.key command. | adb shell rm /knowledge/system/password.key |
| adb reboot | Restarts the Android gadget. | Essential after working unlock instructions. | adb reboot |
Manufacturing facility Resetting the System: How To Unlock My Android Telephone With out Pin
Alright, so you have exhausted your choices, and also you’re staring down the barrel of a locked telephone. Manufacturing facility resetting your gadget is like hitting the large pink reset button – it wipes every thing clear, together with that pesky PIN. It’s kind of drastic, however it may be a lifesaver when all else fails. Consider it as a recent begin, a digital decluttering, or, for those who’re feeling dramatic, a phoenix rising from the ashes of forgotten passwords.
Simply be warned: this technique is a data-wipe.
Getting into Restoration Mode for Completely different Android Telephone Manufacturers
The journey to manufacturing unit resetting your telephone entails getting into one thing known as “restoration mode.” It is a particular boot atmosphere that lets you carry out system-level duties, together with wiping your gadget. The method to entry restoration mode varies relying in your telephone’s producer, so let’s break it down by model. Get able to flex these finger muscle tissues, as a result of timing is every thing.
- Samsung: First, energy off your gadget utterly. Subsequent, press and maintain the Quantity Up button, the Bixby button (in case your telephone has one), and the Energy button concurrently. Maintain holding them till the Samsung emblem seems, then launch the Energy button, however proceed holding the opposite two till the restoration mode display seems. You may see a menu with choices like “wipe knowledge/manufacturing unit reset.”
- Google Pixel: Flip off your Pixel. Then, press and maintain the Quantity Down button and the Energy button on the similar time. Maintain holding them till you see the bootloader display. Use the quantity buttons to navigate to “Restoration mode” and choose it utilizing the Energy button.
- LG: Energy off your LG telephone. Press and maintain the Quantity Down button and the Energy button concurrently. Launch the Energy button when the LG emblem seems, however proceed holding the Quantity Down button. As soon as the restoration mode display reveals up, launch the Quantity Down button.
- Motorola: Swap off your Motorola telephone. Press and maintain the Quantity Down button and the Energy button till the boot mode display seems. Use the quantity buttons to navigate and the Energy button to pick out “Restoration mode.”
- OnePlus: Flip off your OnePlus telephone. Press and maintain the Quantity Down button and the Energy button concurrently. Launch the Energy button when the OnePlus emblem seems, however maintain holding the Quantity Down button till you see the restoration mode display.
- Xiaomi/Redmi/POCO: Energy off your Xiaomi, Redmi, or POCO gadget. Press and maintain the Quantity Up button and the Energy button on the similar time. Launch the Energy button when the Mi emblem seems, however proceed holding the Quantity Up button till you enter restoration mode.
As soon as in restoration mode, you will navigate the menu utilizing the quantity buttons to maneuver and the facility button to pick out. The precise wording of the manufacturing unit reset choice might differ barely, however search for one thing like “wipe knowledge/manufacturing unit reset” or “manufacturing unit reset.” After choosing this, affirm your selection (often by choosing “sure” or “affirm”). The telephone will then erase all knowledge and return to its manufacturing unit settings.
Penalties of a Manufacturing facility Reset and Information Loss
Okay, this is the truth test: a manufacturing unit reset is a digital eraser. Every little thing in your telephone – pictures, movies, contacts, apps, every thing – might be gone. Consider it as a whole do-over, a recent canvas, a clear slate. Because of this backing up your knowledge beforehand is essential. And not using a backup, you are basically ranging from scratch.
Contemplate this a cautionary story, a lesson in digital preparedness.
Backup Earlier than You Leap:
- Google Account Backup: Guarantee your telephone is backing as much as your Google account. This sometimes consists of contacts, calendar occasions, and app knowledge. Go to Settings > Accounts > Google and confirm that sync is enabled.
- Native Backup: Use your telephone’s built-in backup function to create a neighborhood backup on a pc or exterior storage gadget. This typically consists of pictures, movies, and different information. The precise course of varies by producer, however it’s often discovered within the Settings menu beneath “Backup & Restore” or related.
- Cloud Storage: Companies like Google Photographs, Dropbox, or OneDrive can routinely again up your pictures and movies. Guarantee that is enabled earlier than the reset.
Keep in mind, prevention is at all times higher than remedy. Take a second now to again up your knowledge earlier than you end up in a locked-phone predicament. It is a small worth to pay for peace of thoughts and the preservation of your digital reminiscences.
Third-Social gathering Software program and Instruments
Let’s face it, getting locked out of your telephone is a bummer. Within the digital Wild West of the web, a complete ecosystem of software program guarantees to be the important thing to your locked kingdom. Nevertheless, earlier than you click on that obtain button, let’s wade by means of the jungle of third-party instruments claiming to unlock your Android gadget.
The Existence of Third-Social gathering Software program
The digital market is overflowing with software program options marketed as Android unlocking instruments. These applications typically promote the flexibility to bypass PINs, passwords, patterns, and even fingerprint locks. They leverage varied strategies, some legit and others… much less so. They’re promoted throughout web sites, boards, and even video-sharing platforms. You may encounter adverts promising a fast and simple repair in your locked telephone, generally even suggesting it is so simple as plugging it into your pc and hitting a button.
The attraction is comprehensible; who would not desire a fast resolution to a irritating downside?
Evaluating Professionals and Cons of Third-Social gathering Instruments
Selecting to make use of third-party unlocking software program is a choice that requires cautious consideration of the potential advantages and downsides. Weighing the choices is essential.
- Potential Professionals: Some instruments may provide a comparatively simple and probably sooner unlocking course of in comparison with strategies like a manufacturing unit reset, which wipes your knowledge. These instruments might be significantly useful you probably have forgotten your password however have entry to the gadget. Sure applications is likely to be designed to be user-friendly, offering a step-by-step information by means of the unlocking course of.
- Potential Cons: The dangers related to utilizing these instruments are important. Many of those applications are unverified, and their effectiveness is just not assured. They may fail to unlock your gadget, leaving you in the identical locked-out scenario. Some instruments might comprise malware, spy ware, or different malicious software program that may compromise your gadget and steal your private info. Moreover, utilizing unofficial software program might void your gadget’s guarantee.
There’s additionally the moral gray space: utilizing such instruments to entry a tool that is not yours is illegitimate and will result in critical penalties.
Potential Dangers Related to Utilizing Untrusted Software program
The hazards of utilizing third-party unlocking software program typically outweigh the potential advantages. Proceed with warning.
- Malware and Safety Threats: Probably the most important threat is the potential for malware an infection. These instruments can comprise viruses, Trojans, and different malicious software program designed to steal your knowledge, monitor your exercise, and even take management of your gadget. Consider it like this: You are handing the keys to your digital citadel to a stranger.
- Information Loss and Corruption: Unreliable unlocking instruments may cause knowledge loss or corruption. The method might malfunction, resulting in a manufacturing unit reset (which wipes all of your knowledge) or, worse, bricking your gadget, rendering it unusable.
- Privateness Violations: Some software program may gather your private knowledge, together with contacts, pictures, and messages, with out your consent. This knowledge might be used for id theft, monetary fraud, or different malicious functions.
- Authorized and Moral Considerations: Utilizing software program to unlock a tool with out the proprietor’s permission is illegitimate in lots of jurisdictions. Even when it is your individual telephone, using unofficial software program can violate the phrases of service of your cellular supplier or the gadget producer.
- Bricking Your System: Within the worst-case situation, the software program might corrupt your gadget’s working system, rendering it unusable, often known as “bricking” the gadget. That is typically an irreversible consequence.
Utilizing Biometric Authentication (If Out there)
Ah, the candy aid of a fingerprint or a look! Biometric authentication, like a secret handshake along with your telephone, might be your digital key whenever you’ve forgotten your PIN. This technique leverages the distinctive bodily traits of your physique to grant entry, providing a handy and sometimes faster different to getting into a code. It is like having a personalised VIP cross to your digital world.
Unlocking with Biometrics
When you’ve beforehand arrange fingerprint or facial recognition, and the system is working, that is your golden ticket. The method is easy: merely place your registered finger on the fingerprint sensor or have a look at the front-facing digital camera. In case your biometric knowledge matches the saved info, your telephone unlocks. If it would not, you will be prompted to enter your backup PIN, sample, or password – a failsafe to maintain your knowledge safe.
It’s kind of like having a lock that requires each a key and a backup key, simply in case the primary one goes lacking.
Setting Up Biometric Authentication
Establishing biometric authentication is often a breeze. It is like instructing your telephone to acknowledge you. Right here’s a normal information; particular steps might differ barely relying in your Android gadget’s producer and Android model:
- Navigate to Settings: Open your telephone’s Settings app. Search for a piece associated to safety, biometrics, or passwords and safety.
- Select Your Technique: Choose both “Fingerprint” or “Facial Recognition,” relying on what your telephone provides.
- Enroll Your Information: Observe the on-screen directions to enroll your fingerprint or face. This sometimes entails inserting your finger on the sensor a number of instances from completely different angles or positioning your face inside a body for the digital camera. For facial recognition, make sure you’re in a well-lit atmosphere.
- Set Up a Backup: The system will doubtless immediate you to arrange a backup PIN, sample, or password. That is important, because it’s your lifeline if the biometric authentication fails (e.g., in case your finger is moist or the facial recognition would not acknowledge you).
- Customise Settings: Discover the settings in your chosen biometric technique. You may discover choices to allow or disable the function for unlocking your telephone, authorizing purchases, or logging into apps.
It is essential to recollect the backup technique, because it’s the one technique to regain entry if the biometric authentication fails. It is just like having a spare key hidden in a secure place.
Safety Concerns of Biometric Authentication
Whereas handy, biometric authentication has its personal set of safety issues. Let’s delve into them:
- Spoofing Vulnerability: Fingerprint sensors can generally be tricked utilizing copies of fingerprints. Facial recognition programs might be fooled by high-quality images and even 3D masks. Whereas these assaults are sometimes refined, it is a vulnerability to pay attention to.
- Information Storage: Biometric knowledge is saved in your gadget, not within the cloud (typically). It is a good factor for privateness, however it additionally signifies that in case your gadget is compromised, your biometric knowledge might be in danger.
- Reversibility: In contrast to a PIN, your fingerprint or face can’t be modified. In case your biometric knowledge is compromised, you may’t merely change your fingerprint. You’d should depend on different safety measures.
- Liveness Detection: Trendy facial recognition programs typically make use of liveness detection, which means they attempt to decide if the face is definitely a stay particular person and never {a photograph} or masks. Nevertheless, this know-how is not foolproof.
- False Positives/Negatives: Fingerprint sensors and facial recognition programs can generally fail to acknowledge you (false negatives) or, in uncommon instances, acknowledge another person (false positives). The accuracy of those programs will depend on the standard of the {hardware} and the software program algorithms.
The safety of biometric authentication will depend on a number of elements, together with the standard of the sensor or digital camera, the sophistication of the algorithms used, and the safety of your gadget. It’s a highly effective software, however it’s not an ideal one.
Biometric authentication is sort of a highly effective safety guard, at all times on responsibility, however it’s necessary to do not forget that it is only one layer of protection. The backup PIN, sample, or password is your trusty sidekick, at all times able to step in when the safety guard wants a break. It is about balancing comfort with vigilance.
Troubleshooting Frequent Points
Generally, even with the most effective laid plans, issues go awry. Unlocking your Android telephone with out a PIN could be a journey, and like several journey, it is sure to have a number of bumps within the highway. This part dives into among the commonest pitfalls and gives options that will help you navigate them.
Discover My System Malfunctions
The “Discover My System” function, whereas a lifesaver, is not at all times as dependable as we would like. There are a number of the explanation why it may not work, and figuring out how one can troubleshoot them is essential.First, guarantee your telephone is related to the web. “Discover My System” depends on an energetic web connection (both Wi-Fi or cellular knowledge) to speak with Google’s servers. With out it, the service is successfully ineffective.
Consider it like attempting to ship a letter with out a stamp; it merely will not attain its vacation spot.Subsequent, confirm that “Discover My System” is enabled in your telephone. This setting is commonly toggled off by default, or it might need been inadvertently disabled. You may often discover this setting inside your Google account settings on the telephone itself or by way of the Google account settings on a pc.Lastly, take into account the potential of location providers being disabled.
“Discover My System” wants location providers enabled to pinpoint your telephone’s whereabouts. Double-check that location providers are turned on and that the “Discover My System” app has permission to entry your location.
- Telephone is powered off: “Discover My System” can solely find a powered-on telephone. In case your telephone is off, it can present the final recognized location.
- Telephone is out of vary: If the telephone is just not related to the web, “Discover My System” cannot perform.
- Manufacturing facility reset: A manufacturing unit reset erases all knowledge, together with the connection to “Discover My System,” rendering it ineffective.
ADB Connection Failures
ADB (Android Debug Bridge) is a robust software, however it may be irritating when it would not cooperate. A number of elements may cause ADB to fail, and addressing them requires a scientific method.One of the widespread culprits is inaccurate drivers. Be sure to have the proper USB drivers put in in your particular telephone mannequin in your pc. These drivers permit your pc to speak along with your telephone.
A fast seek for “[your phone model] USB drivers” ought to lead you to the suitable obtain.One other frequent problem is unauthorized debugging. In your telephone, you must allow USB debugging within the developer choices. You might also have to authorize your pc to entry the telephone by way of an on-screen immediate whenever you join it. When you do not see the immediate, unplug and replug the telephone, and ensure to pick out “All the time permit from this pc” to keep away from this step sooner or later.The connection itself can be problematic.
Guarantee you’re utilizing a working USB cable and that it is securely related to each your telephone and your pc. Attempt a unique USB port in your pc, as some ports might have points.
- Incorrect drivers: Guarantee the proper USB drivers in your telephone mannequin are put in.
- USB debugging not enabled: Allow USB debugging in developer choices in your telephone.
- Unauthorized debugging: Authorize your pc when prompted in your telephone.
- Cable points: Attempt a unique USB cable or port.
- ADB not put in or configured appropriately: Confirm ADB is put in appropriately and that the trail is ready up in your system’s atmosphere variables.
Restoration Mode Entry Issues
Getting into restoration mode is crucial for sure unlocking strategies, similar to manufacturing unit resets. In case your telephone refuses to enter restoration mode, it may be a big roadblock.Step one is to make sure you are utilizing the proper button mixture. This varies relying on the telephone producer and mannequin. A fast on-line seek for “[your phone model] restoration mode button mixture” ought to present the required info.
Frequent mixtures contain urgent and holding the facility button and the quantity up or quantity down button concurrently.If the button mixture appears appropriate however would not work, there is likely to be a {hardware} problem. In some instances, a broken energy or quantity button can stop you from getting into restoration mode. Attempt urgent the buttons firmly and repeatedly.One other risk is a software program glitch.
Attempt restarting your telephone and trying the button mixture once more. In uncommon instances, a corrupted working system can intrude with restoration mode.
- Incorrect button mixture: Double-check the proper button mixture in your telephone mannequin.
- {Hardware} points: Examine the facility and quantity buttons for injury.
- Software program glitches: Restart your telephone and take a look at once more.
- Customized ROMs or modifications: When you’ve got a customized ROM put in, the restoration mode entry is likely to be completely different. Seek the advice of the ROM’s documentation.
Prevention and Finest Practices
Alright, let’s speak about holding your Android telephone locked down tight so that you hopefully by no means should undergo the headache of unlocking it with out your PIN. It is a lot simpler to stop the issue than to repair it, proper? We’ll cowl some easy tips for remembering your PINs and passwords, after which dive into some good habits that’ll maintain your telephone safe.
Suggestions for Remembering PINs and Passwords
Remembering your PIN and passwords can generally really feel like attempting to recall the identify of that actor in that one film – irritating! Nevertheless, a bit of little bit of planning and some reminiscence tips could make all of the distinction.Listed below are some helpful suggestions:
- Select one thing significant: Do not choose one thing random like “1234” or “0000”. These are the primary mixtures hackers strive. As an alternative, select a PIN that pertains to one thing you will simply bear in mind, such because the 12 months your favourite band was fashioned or a big date.
- Use a sample: When you want a sample unlock, select one which’s advanced however straightforward so that you can visualize. Take into consideration the trail you are taking to work or the Artikel of a well-known object.
- Write it down (safely): When you completely
-must* write it down, maintain it in a safe location, like a password supervisor app (extra on these later) or a bodily pocket book locked away. By no means retailer it in your telephone in a notice that is not encrypted. - Observe makes good: The extra you utilize your PIN or password, the extra ingrained it can turn out to be in your reminiscence. Attempt unlocking your telephone a number of instances a day.
- Keep away from widespread errors: Do not use private info that is simply accessible to others, like your birthday or the names of your loved ones members. This makes it simpler for somebody to guess your PIN.
- Overview and refresh: Periodically, assessment your PIN and take into account altering it, particularly for those who suppose it might need been compromised.
Finest Practices for Securing an Android Telephone
Securing your Android telephone is not simply concerning the PIN. It is about constructing layers of safety. Consider it like a fortress, with a number of partitions and moats. Here is how one can construct your digital fortress:
- Allow Display Lock: That is your first line of protection. All the time have a PIN, sample, password, or biometric lock enabled. It is the naked minimal.
- Use a Robust Password: When you’re utilizing a password as a substitute of a PIN or sample, make it lengthy, advanced, and distinctive. A mixture of higher and lowercase letters, numbers, and symbols is right.
- Two-Issue Authentication (2FA): Allow 2FA wherever attainable. This provides an additional layer of safety by requiring a second verification technique, like a code despatched to your telephone or e-mail, along with your password.
- Maintain Software program Up to date: Commonly replace your Android working system and all of your apps. Updates typically embody safety patches that repair vulnerabilities. That is like repairing the partitions of your fortress whenever you spot a crack.
- Be Cautious with Wi-Fi: Keep away from connecting to public, unsecured Wi-Fi networks, as they could be a haven for hackers. When you should use public Wi-Fi, use a Digital Non-public Community (VPN) to encrypt your web site visitors.
- Set up Apps from Trusted Sources: Solely obtain apps from the Google Play Retailer or different respected sources. Be cautious of apps from unknown builders or web sites, as they might comprise malware.
- Overview App Permissions: Take note of the permissions you grant to apps. Does an app actually need entry to your location, contacts, or digital camera? If not, deny the permission.
- Again Up Your Information: Commonly again up your telephone’s knowledge, together with contacts, pictures, and paperwork. It is a security web in case your telephone is misplaced, stolen, or broken. Use Google Drive or an analogous service.
- Use a Password Supervisor: A password supervisor can securely retailer your passwords and routinely fill them in whenever you want them. This makes it simpler to make use of sturdy, distinctive passwords for every of your accounts.
- Be Conscious of Phishing: Be cautious of suspicious emails, textual content messages, and telephone calls that ask in your private info. By no means click on on hyperlinks or present info except you’re sure the request is legit.
- Allow Discover My System: This function lets you find, lock, or erase your telephone remotely if it is misplaced or stolen. It is an important safety measure.
Suggestions to Keep away from the Have to Unlock Your Telephone And not using a PIN within the Future
To additional solidify your defenses and keep away from the frustration of a locked-out telephone, listed here are some proactive measures:
- Memorize Your PIN/Password: That is probably the most important step. Make it a behavior. Use the guidelines above.
- Commonly Change Your PIN/Password: Contemplate altering your safety credentials each few months or whenever you suspect a possible breach. That is like rotating the guards on the gate.
- Use Biometric Authentication: In case your telephone helps it, use fingerprint or facial recognition as your main unlock technique. It is often extra handy and safe than a PIN or password.
- Be Aware of Your Telephone’s Setting: Do not depart your telephone unattended in public locations. Defend it from bodily injury, which might make it simpler to bypass safety measures.
- Educate Your self About Safety Threats: Keep knowledgeable concerning the newest safety threats and scams. Information is your greatest protection. Learn respected tech blogs, safety information websites, and comply with cybersecurity consultants.
- Observe Good Digital Hygiene: Be conscious of what you click on, what you obtain, and the place you browse. A bit warning goes a good distance. Suppose earlier than you click on!
- Take a look at Your Safety: Periodically take a look at your telephone’s safety settings. Attempt to entry it with out your PIN to make sure every thing is working as anticipated.
- Have a Plan for Loss or Theft: Know what steps to take in case your telephone is misplaced or stolen. This consists of instantly reporting it to your service, utilizing Discover My System to find it, and altering your passwords.
Visible Aids and Illustrations
![3 Fast Ways to Reset Android Phone Without PIN [2025 Guide] - EaseUS How to unlock my android phone without pin](https://i0.wp.com/mobi.easeus.com/images/en/screenshot/mobiunlock-resource/theme-unlock-motorola-without-google-account.png?w=700)
Visible aids are essential when navigating the generally advanced world of unlocking a locked Android telephone. They assist make clear procedures, demystify interfaces, and supply a transparent understanding of the steps concerned. Let’s delve into some illustrative examples.
Discover My System Interface on a Pc
The ‘Discover My System’ interface, accessible by way of an online browser on a pc, presents a clear and purposeful structure designed for ease of use. This part explains the important thing options of a typical ‘Discover My System’ interface, aiding in understanding its functionalities.The interface sometimes shows a map, prominently that includes the final recognized location of the locked Android gadget. The map makes use of an ordinary mapping service, permitting for zooming and panning to pinpoint the gadget’s location with accuracy.
- On the left aspect of the interface, you will discover a panel with gadget info. This consists of:
- The gadget’s identify (as set by the consumer).
- The gadget’s mannequin.
- The battery degree, indicated by a proportion and a battery icon.
- A standing message indicating whether or not the gadget is on-line or offline.
- Under the gadget info, there are three main choices:
- Play Sound: This function triggers a ringing sound on the gadget, even when it is set to silent or vibrate, making it straightforward to find if it is close by.
- Safe System: This feature lets you lock the gadget with a brand new PIN or password, and likewise shows a customized message on the lock display, similar to contact info for the finder.
- Erase System: That is probably the most drastic choice, which manufacturing unit resets the gadget, wiping all knowledge. A affirmation immediate is often required earlier than continuing, warning customers that knowledge restoration might not be attainable.
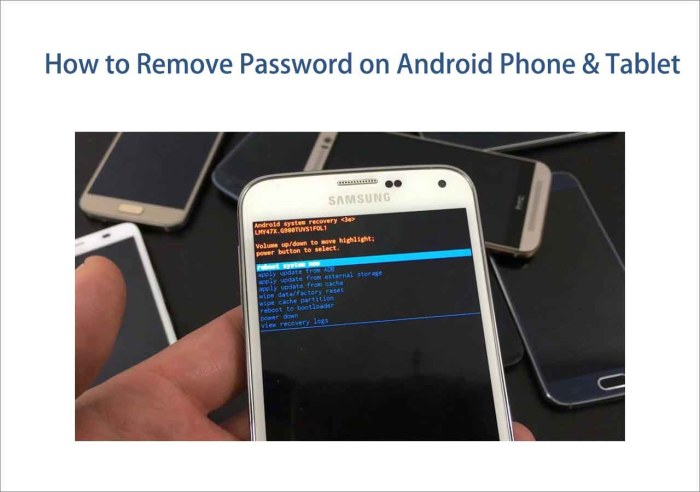
Android Telephone in Restoration Mode
Restoration mode is a particular boot atmosphere on Android gadgets, providing instruments to troubleshoot and carry out superior operations. A picture of a telephone in restoration mode sometimes showcases a text-based menu with varied choices.The picture would depict a black or dark-colored display with white textual content, offering clear distinction for readability. The menu choices are often introduced in an inventory format.
- Reboot system now: That is the default choice, restarting the telephone and exiting restoration mode.
- Reboot to bootloader: This feature lets you boot into the bootloader, which is one other superior atmosphere.
- Apply replace from ADB: That is used to put in updates by way of a pc utilizing the Android Debug Bridge (ADB) software.
- Apply replace from SD card: This lets you set up updates from a microSD card.
- Wipe knowledge/manufacturing unit reset: This significant choice wipes all consumer knowledge and settings, returning the gadget to its authentic manufacturing unit state. A affirmation step is often required to stop unintentional knowledge loss.
- Wipe cache partition: This feature clears the cache partition, which may resolve some efficiency points.
- Mount /system: Permits mounting the system partition.
- View restoration logs: Shows logs associated to the restoration course of.
- Run graphics take a look at: Exams the gadget’s graphics capabilities.
- Energy off: Shuts down the gadget.
ADB Line Interface with Unlock Highlighted
The Android Debug Bridge (ADB) interface is a command-line software used for interacting with an Android gadget. Visualizing the method of unlocking the gadget by way of ADB helps make clear the instructions concerned.The picture presents a terminal window, sometimes with a black background and white textual content. The main target is on a selected command sequence that can be utilized to unlock the gadget.The ADB interface showcases the next key parts:
- The command immediate, indicating the present listing or gadget connection standing.
- The ADB command being executed, which is likely to be one thing like:
- The output from the command, which might be a easy affirmation message, or in some instances, a extra detailed response indicating success or failure.
- Contextual info, such because the gadget’s serial quantity (masked for privateness) and the ADB model.
adb shell rm /knowledge/system/gesture.key
